Successfully Mitigate Risks That Can Harm Your Business
Avoid potential risks by keeping track of your competitors and staying up-to-date on technological trends using LexisNexis® PatentSight+® patent analytics.
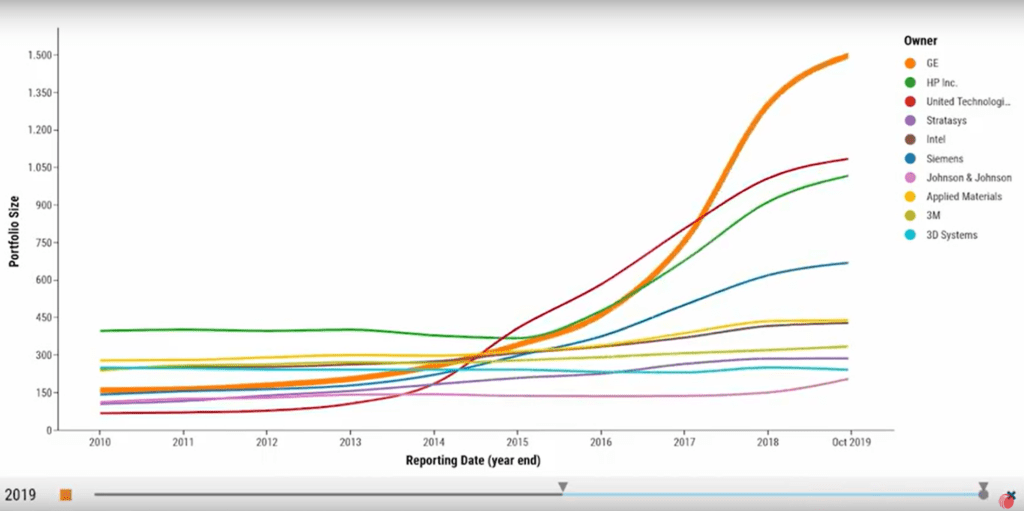
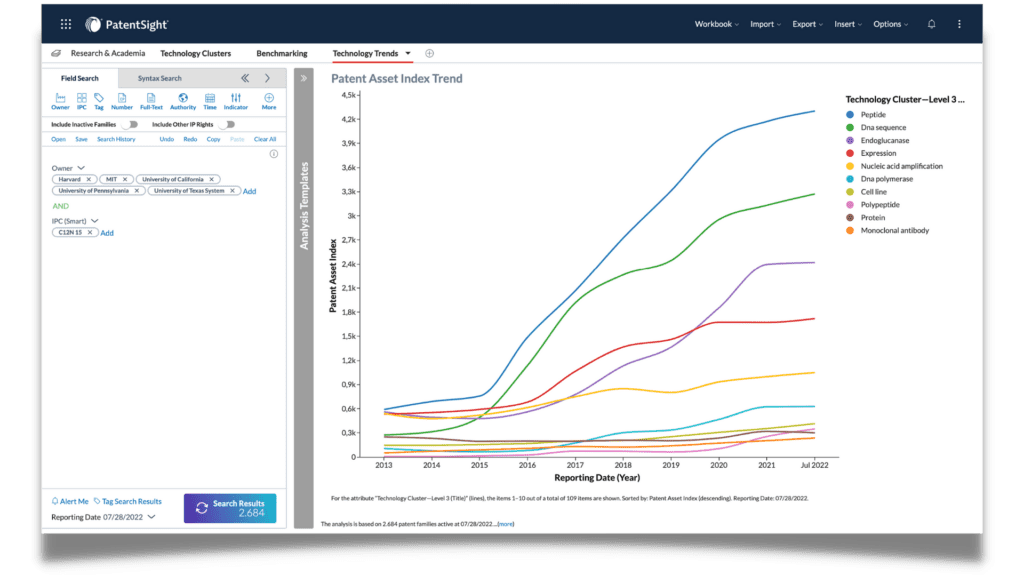
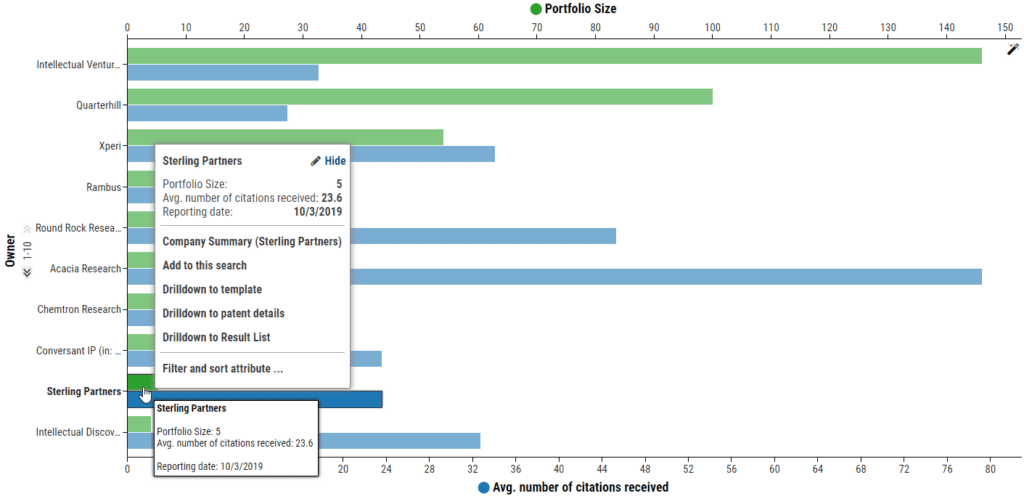
Keep track of your competitors in your target technology fields
Imagine that a competitor has been filing strongly for the past five years and is building the largest portfolio in one of your core technology fields as GE did in the tech field of Additive Manufacturing (see video to the left). LexisNexis PatentSight+ helps you identify filing increments with ease.
Would you like to learn more?

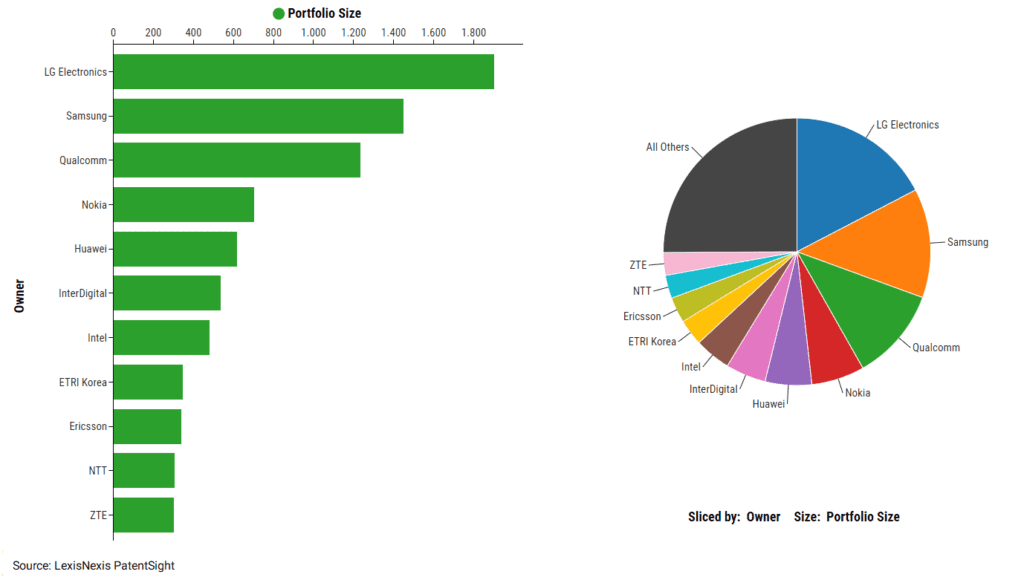
Want to better understand China’s increasing dominance across the Engineering industry?
Download our Engineering intellectual property report, where data reveals clear trends about the future of Engineering and how international players are reacting to the growing Chinese influence.
Get insights into different Engineering sectors, including Aviation, Energy, Manufacturing Equipment, Railway and Ship Building, Civil Engineering, and more.
Unlock the true value of your portfolio
Learn how to profit from sophisticated patent analysis.

We would love to get to know you and show you some invaluable insights into the IP landscape:
- Let’s have a conversation about your current priorities in IP analytics.
- Get an external view of your portfolio.
- Learn how others see you and survey other market players from a new perspective.
Submit the form, and we’ll be in touch.